The LOADALL Instruction
by
Robert Collins
Of the few undocumented instructions in the 80286 and 80386 microprocessors, the LOADALL instruction is the most widely known. Nevertheless, very few people understand how to use it. Using LOADALL is not as simp)e as merely knowing the LOADALL opcode and its format, because knowing how to use LOADALL requires a knowledge of many aspects of the CPUs' behavior that are not documented in their respective data sheets.
The 286 LOADALL is widely known because a 15-page lntel confidential document describing its use was given to many developers. 286 LOADALL is so commonly used in production code that DOS 3.3 (and above) and OS/2 have provisions for using LOADALL built in them. Every 386 and 486 BIOS emulates 286 LOADALL and even Microsoft CODEVIEW recognizes the 286 LOADALL opcode and disassembles it.
On the other hand, the 386 LOADALL is not widely known, and very few developers even know it exists. In this article, I will explain how to use both the 286 and 386 LOADALL instructions and present source code to demonstrate the various aspects of CPU behavior that become apparent, or can be proven, when using LOADALL.
| Intel originally included LOADALL
in the CPU mask for testing purposes and In Circuit
Emulator (ICE) support. As its name implies, LOADALL loads
all of the CPU registers, including the
"hidden" software-invisible registers. At the
completion of a LOADALL instruction, the entire
CPU state is defined according to the LOADALL data
table. LOADALL loads all of the software-visible
registers such as AX, and all of the
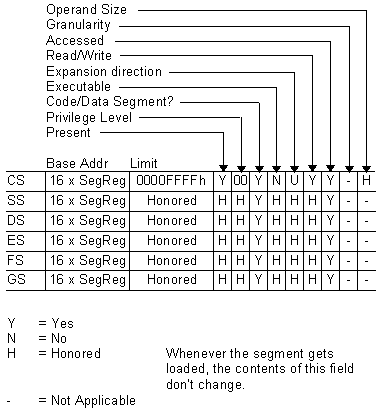
software-invisible registers such as the segment descriptor caches. By manipulating the descriptor cache base registers, you can access the entire address space without switching to protected mode. In other words, by using LOADALL, you can access memory above 1Mb from real mode. Since the alternative method for the 286 (switching to protected mode, accessing the desired memory, then resetting the CPU - the only way to get the 286 back to real mode) has a significant performance penalty, LOADALL is most significant to 286 programmers. LOADALL provides them with a new capability that is not available by any other means. LOADALL Details LOADALL is closely coupled with the CPU hardware. Both the 286 and 386 have different internal hardware and Intel implemented LOADALL using different opcodes on the 286 and 386. 80286 LOADALL (opcode 0F05) produces an invalid opcode exception when executed on the 386, and 80386 LOADALL (opcode 0F07) produces an invalid opcode exception when executed on the 286. LOADALL loads all CPU registers (including MSW, GDTR, CSBASE, ESACCESS) from a memory image. You can execute LOADALL in real or protected mode, but only at privilege level 0 (CPL=0). If you execute LOADALL at any other privilege level, the CPU generates an exception. By directly loading the descriptor cache registers with LOADALL, a program has explicit control over the base address, segment limit, and access rights associated with each memory segment. Normally, the CPU loads these values each time it loads a segment register, but LOADALL allows you to load these hidden registers independently of their segment register counterparts. In real mode, LOADALL makes it possible to access a memory segment that is not associated with any segment register. Likewise in protected mode, you can access memory that has no descriptor table entry. LOADALL performs no protection checks against any of the loaded register values. When you execute it at CPL 0, LOADALL can generate no exceptions. The segment access rights and limit portions may be values that would otherwise be illegal in the context of real mode or protected mode, but LOADALL willingly loads these values with no checks. Once loaded, however, the CPU performs full access checks when accessing a segment. For example, you can load a segment whose access is marked "not present." Normally, this condition would generate exception 11, "segment not present", but LOADALL does not generate exception 11. Instead, any attempt to access this segment will generate exception 13. LOADALL does not check coherency between the software-visible segment registers and the software-invisible segment descriptor cache registers. Any segment descriptor base register may point to any area in the CPU address space, while the software-visible segment register may contain any other arbitrary value. The CPU makes all memory references according to the descriptor cache registers, not the software-visible segment registers. All subsequent segment register loads will reload the descriptor cache register. Beware of using values in CS that do not perfectly match a code segment descriptor table entry, or a real mode code segment - an interrupt return (IRET) may either cause an exception or execution to resume at an unexpected location. Likewise, pushing and subsequently popping any segment register will force the descriptor cache register to reload according to the CPU's conventional protocol, thereby inhibiting any further real mode extended memory references. 80286 LOADALL You encode the 80286 LOADALL as a two-byte opcode, 0F05h. LOADALL reads its table from a fixed memory location at 800h (80:0 in real-mode addressing). LOADALL performs 51 bus cycles (WORD cycles), and takes 195 clocks with no wait states. Table 1 shows the format you must prepare at location 800h before executing the 286 LOADALL instruction. All CPU register entries in the LOADALL table conform to the standard Intel format, where the least significant byte is at the lowest memory address. Table 2 shows the 286 format of the descriptor cache entries.
Intel recommends some guidelines for proper execution following LOADALL. The stack segment should be a read/write data segment; the code segment can be execute on1y (access=95h), read/execute (access=9bh), or read/write/execute (access=93h). Proper protected mode operation also requires that the DPL of CS and DPL of SS be equal. These attributes determine the CPL of the processor. Also, the DPL fields of ES and DS should be equal to 3 to prevent RETF or IRET instructions from zeroing these registers. The code in listing 1 demonstrates how to exp1ore the various operating modes with 286 LOADALL and how to access extended memory while in real mode. The LOADALL test performs various functions that would be impossible to duplicate without using LOADALL. 80386 LOADALL The 386 LOADALL is encoded as a two-byte opcode (0F07). Unlike the 286 LOADALL, this LOADALL instruction reads its data from a table pointed to by ES:EDI. Segment overrides are allowed, but apparently ignored. The 386 LOADALL performs 51 bus cycles (DWORD cycles) and takes 122 clocks with no wait states. Table 3 shows the 386 LOADALL format. However, Table 3 does not show that prior to reading the LOADALL table, LOADALL reads 10 DWORDs exactly 100h bytes beyond the beginning of the table (ES:EDI+100h). This data is not used to load any of the registers LOADALL does not load (CR2, CR3, DRO-DR3, TR6, TR7), or the Numeric Processor eXtension (NPX). At this time, the purpose of reading this data and its destination is a mystery. Figure 1 shows an ICE trace showing all the bus cycles associated with LOADALL's execution. As with the 286 LOADALL, all CPU register entries in the LOADALL table are in the standard Intel format where the least significant byte is at the lowest memory address. The 386 descriptor cache entries have the format shown in Table 4. Listing 2 shows how to test 386 LOADALL. This test is more comprehensive than the 286 LOADALL test because of the expanded capabilities of the 386 microprocessor. This test puts the CPU into various states that are illegal and are impossible to duplicate through any other software means. LOADALL Emulation Due to the large number of systems programs that use 286 LOADALL, all 386 and 486 BIOS's must emu1ate the 286 LOADALL instruction (opcode 0F05). On the 386 and 486, the 286 LOADALL instruction generates an invalid opcode exception. The BIOS traps this exception and does its best to emulate the functionality of the LOADALL instruction, but perfect emulation is impossible without using LOADALL itself. Using 386 LOADALL to emulate 286 LOADALL can be done, but has its risks. First of all, the 486 does not have a LOADALL instruction. Second, Intel has threatened to remove LOADALL from the 386 mask. Perfect emulation is possible on the 386 by using 386 LOADALL to emulate 286 LOADALL. Listing 3 shows a TSR program that uses 386 LOADALL to emulate 286 LOADALL. The program first tests that you are a 386 before insta1ling itself. By using this emu1ation program, you can guarantee perfect 286 LOADALL emulation. Conclusion LOADALL is a very powerful instruction, but the features that make it so powerful also make it risky. For example, LOADALL can put the processor in states that are otherwise impossible to duplicate through any other software means. Using LOADALL requires a thorough understanding of how the CPU processes register loads, the ramifications of those register loads, and careful planning. The illegally induced processor states can easily cause system crashes if not properly planned for. The best way to avoid system crashes is to avoid using LOADALL unless you are totally confident in your understanding of the CPU and in your programming skills. The 286 LOADALL is described in a 15-page Intel-confidential document The document describes in detail how to use the instruction, and also describes many of its possible uses. LOADALL can be used to access extended memory while in real mode, and to emulate real mode while in protected mode. Programs such as RAMDRIVE, ABOVEDISC, and OS/2 use LOADALL. DOS 3.3 has provisions for using LOADALL by leaving a 102-byte 'hole' at 80:0. If you are a systems programmer and have a need to know this information, Intel will provide it, along with source code to emulate 286 LOADALL on the 386 (without using 386 LOADALL). Unlike the 286 LOADALL, the 386 LOADALL is still an Intel top secret. l do not know of any document that describes its use, format, or acknowledges its existence. Very few people at Intel wil1 acknowledge that LOADALL even exists in the 80386 mask. The official Intel line is that, due to U.S. Military pressure, LOADALL was removed from the 80386 mask over a year ago. However, running the program in Listing-2 demonstrates that LOADALL is alive, well, and still available on the latest stepping of the 80386. View source code for 286 LOADALL: View source code for 386 LOADALL: View source code for EMULOAD (286 LOADALL
emulation using 386 LOADALL): Download entire source code archive for 286LOAD,
386LOAD, and EMULOAD: |
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||